Hey Guys, in this module, we are going to talk about What is SSL (Secure Socket Layer), Since we all work over the internet and we want a secure connection to be established between us and the clients so that our data and information are safe.
So, to achieve this let’s start reading this module in dept.
What is SSL (Secure Socket Layer)?
SSL or Secured Socket Layer is an internet security protocol with an encryption-based technique. It was first developed by Netscape in the mid-1990s, the main purpose of this was to ensure privacy, data integrity, and authentication in communications through the Internet.
TLS or Transport Layer Security, the descendent of the SSL, has provided security and encryption, because of which all modern internet commerce and communications are possible. It provides continuous updates to keep pace or an eye on the sophisticated attacker.
These two protocols are used for establishing encrypted and authenticated links between computer networks.
What is the difference between TLS and SSL?
The difference between this TLS protocol and SSL 3.0 is not dramatic. The name of both TLS and SSL are different because it signifies a change in ownership. Thus, it’s not the case that there is a difference between TLS and SSL, they two just form a continuously updated series of protocols and often are called together as SSL/TLS. The next version of SSL was released in 1999, and it was standardized by the Internet Engineering Task Force (IETF) and was named TLS or Transport Layer Security.
All types of internet traffic are encrypted by TLS protocol, and among them the most common is web traffic. If the URL in your address starts with “HTTPS”, then that means your browser is connected via TLS, and there is one indicator with a padlock that tells that your connection is secure. But with TLS, it can be used by various other applications as well like Usenet and e-mail.
Both of them are very closely related, therefore these two terms are often confused and used interchangeably. Some people use SSL/TLS encryption while some use SSL to refer to TLS because SSL has so much name recognition.
Why do we need SSL?
We all indulge online and do all our work online, even all communications and transactions are also being done online, So, there is very little reason not to use SSL. Here, I am mentioning some of the points that why SSL is important. SSL follows these types of security information.
Data Integrity: It checks for the safety of data, its consistency, accuracy, and completeness.
Encryption: It is used to protect the transmission of data for example server to server, browser to the server, application to the server, etc.
Authentication: It checks whether you are connected to the correct server or not.
Where can we use SSL?
SSL is used to secure many things and is used widely. Some of them are mentioned below.
- It is used to secure Intranet-based traffic, such as file sharing, database connections, internal networks, and extranets.
- Online payments or online credit card transactions.
- Various Webmail servers like Outlook web access, exchange, and office communications server.
- It helps to secure the transfer of files over FTP(s) and HTTPS services, such as transferring large files or website owners uploading or updating a new page to their websites.
- System login to control panels and applications such as cPanel, Parallels, and others.
How SSL Works?
As we have already seen, the SSL protocol is used to make the connection secure. So, now let’s see how SSL works.
SSL works with the following two concepts and that is:
- Asymmetric Cryptography
- Symmetric Cryptography
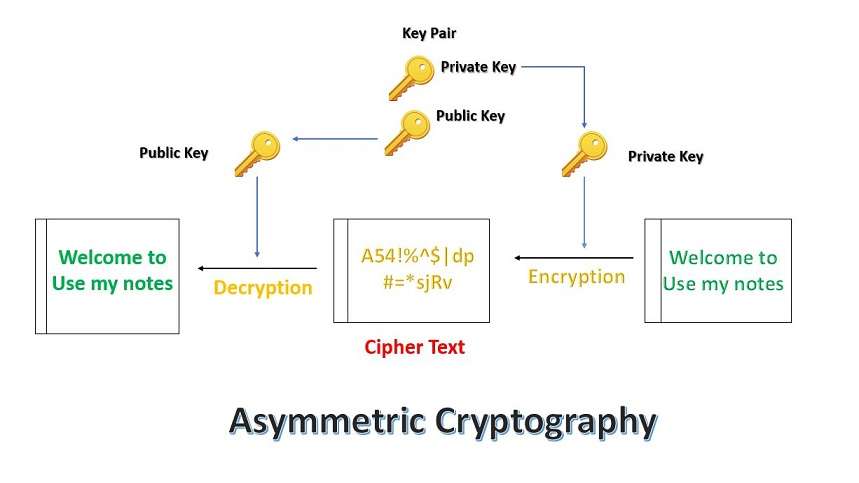
What is Asymmetric Cryptography?
Asymmetric Cryptography is also known as Public-key cryptography or Asymmetric Encryption. It uses a key pair to encrypt or decrypt the data. In a key pair, one is a public key and the other one is a private key. The public key is shared with anyone interested in communication and a private key is kept secret.
The below figure depicts the working of Asymmetric Cryptography.
Here, the keys are created using the mathematical algorithm and use a mathematical value to encrypt or decrypt the data.
SSL uses asymmetric cryptography to initiate the SSL handshake, which is the initial state of starting the communication. Some of the commonly used asymmetric key encryption algorithms are RSA, DSA, ElGamal, and Elliptic curve techniques.
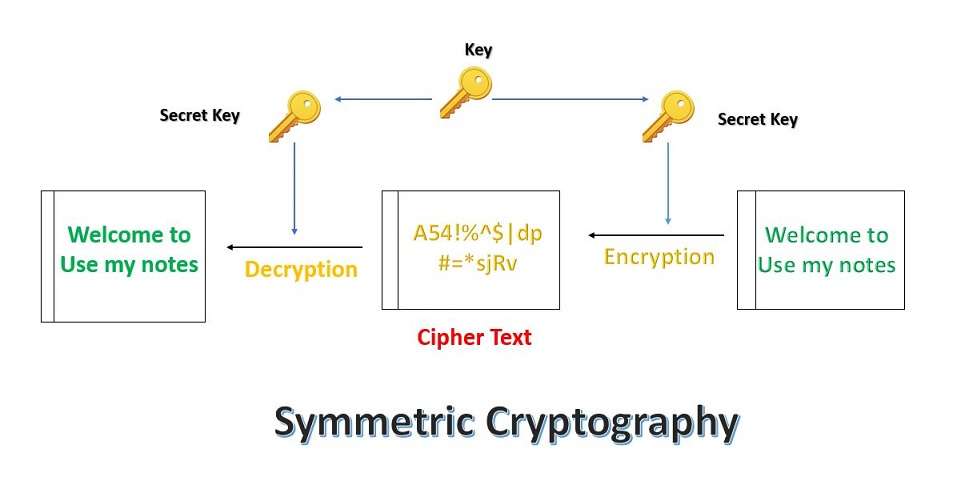
What is Symmetric Cryptography?
Symmetric Cryptography uses only one key which is used for encryption and decryption at both sender and receiver ends. Both sender and receiver should have this key, which should only be known to them.
The below figure depicts the working of Symmetric Cryptography.
It uses this cryptography technique after the initial handshake is done and that too using the session key. Some of the commonly used symmetric algorithms are AES-192, AES-128, and AES-256.
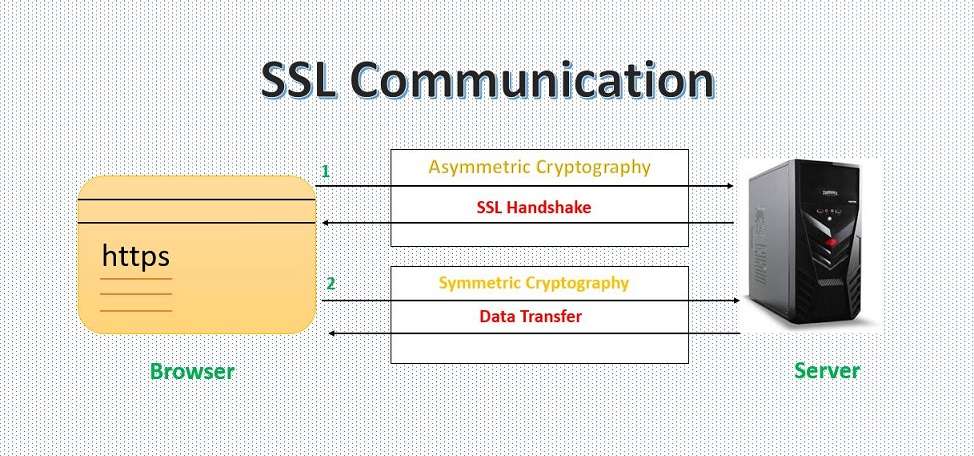
How is the data transferred over the SSL?
The above two mentioned methods are used by the SSL to transfer the data securely over the internet. When SSL communicates between the browser and the web server or between any other two systems, then it is mainly divided into two steps and that is SSL handshake and the actual data transfer.
The figure below illustrates how communication is done through SSL.
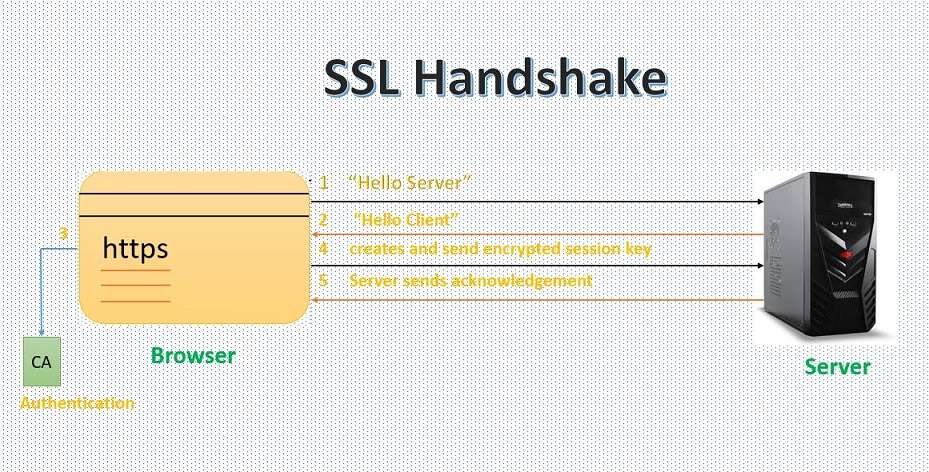
What is an SSL handshake?
All the communications that are done through SSL begin with the handshake. It allows the browser to verify the web server, establish a secure connection and get the public key before the beginning of the data transfer. The SSL handshake is asymmetric cryptography.
Let us understand what is done actually in the above figure.
- The client sends a “Hello Server” message. This includes all the information that needs to communicate with the client using SSL and which are SSL version number, session-specific data, and all.
- The server responds with the “Hello Client” message. This includes all the information that needs to communicate with the server using SSL and which are SSL version number, session-specific data, and all.
- Then the client verifies the SSL certificate of the server from the certificate authority or CA. If in some cases the authentication fails, then the client refuses the SSL connection and if the authentication succeeds, then they will proceed further with step 4.
- Now the client creates a session key, and encrypts it with the server public key, and then sends it to the server. The client will send his certificate to the server if the server will request the client authentication.
- Finally, the server decrypts the session key with its private key and sends the acknowledgment back to the client encrypted with the session key.
Now, in the end, both the client and the server have a valid session key that they can use for further communication and encrypt and decrypt the actual data.
I hope What is SSL (Secure Socket Layer)? the module was very exciting and you all must gain full knowledge about how SSL in cryptography works and what is its importance over the internet and much more information about the same. You all must be excited to read more modules like this, So, stay connected with us. Until then, Stay safe, Keep reading, Stay Happy.