Welcome back. In this module, we will discuss PGP Encryption and Hashing. We will delve into how PGP encryption works and its role in safeguarding data and maintaining security. We’ll explore the advantages and disadvantages of PGP encryption, among other aspects. Let’s begin our exploration of this crucial topic.
So, let’s dive in-depth into this module to start learning.
What is PGP Encryption?
In Cryptography, these techniques are used to help in maintaining privacy for the users and to give more security, so that all can easily work over the internet.
What is PGP Encryption?
PGP encryption also known as Pretty Good Privacy encryption came into existence in 1991, and since then it has become the standard fact for email security. It is a system that is used for both sending encrypted emails as well as sending encrypted sensitive files.
It is a type of program that gives cryptographic authentication and privacy for online communications. It uses a mix of hashing, data compression, and public-key cryptography. Apart from these, it also uses symmetric and asymmetric keys to encrypt the data which is transferred across the networks. The public key and private key features are combined in this.
Different algorithms are used in different steps, and each public key is associated with a unique username and an email address.
PGP is famous because of 2 factors. The first is that the system is available as freeware, and so it spreads rapidly among users who want an extra security level for their email messages. The second is that the PGP uses both public-key encryption and symmetric encryption, it allows users who have never met to send encrypted messages to one another without exchanging the private encryption keys.
How does PGP encryption work?
We know that PGP encryption works by using the combination of two forms of encryption that is public-key encryption and symmetric-key encryption. Let’s see how PGP works.
- Firstly, the PGP encryption generates a random session key by using one of two main algorithms. This key is only used once and this key is a huge number that cannot be guessed.
- Now, the next step is to encrypt the session key. This can be achieved by using the public key of the intended recipient of the message. The public key is tied to a particular person’s identity, which can be used by anyone to send them a message.
- Now the encrypted PGP session key is sent to the recipient by the sender, and they can decrypt the same by using their private key. The recipient can decrypt the actual message using this session key.
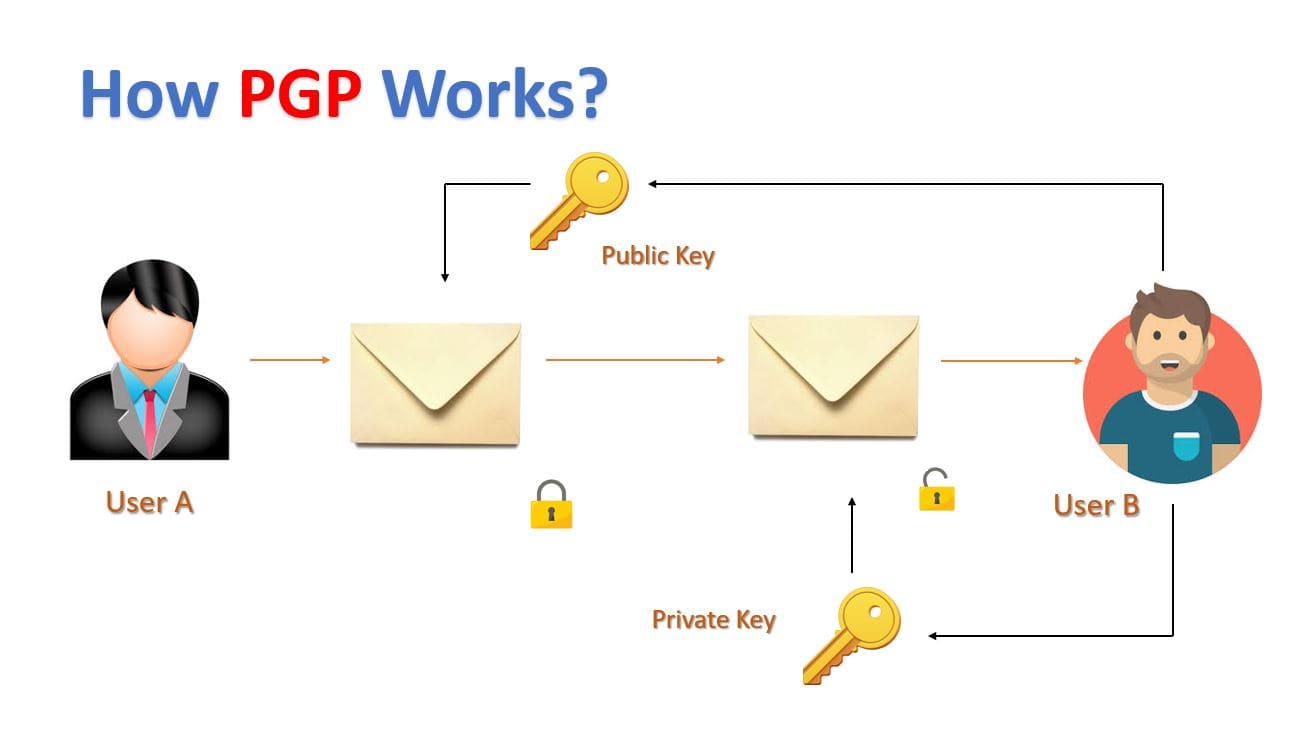
The above figure demonstrates the working of PGP, and that is.
- User A wants to send the message via email to User B.
- Therefore, User B generates the Two keys which are public and private.
- User B sends the public key to User A.
- Then, User A encrypts the message with that public key and sends that message to user B.
- User B then decrypts the message by using the private key.
What is the role of hashing in PGP Encryption?
In Cryptography, Hashing is something that converts a piece of text or data into some unique strings of text. Regardless of the size and type of data, any data can be hashed easily. It is done by using hash functions.
PGP uses a highly cryptographically strong hash function on the plain text that the user is signing. This helps in generating a fixed-length data item which is known as a message digest. The work of the hash function is that it ensures if some of the changes have been done in the data even if it is of one bit, an entirely different output is produced.
What are the uses of PGP Encryption?
Let’s focus on some of the main uses of PGP Encryption.
- You can send the messages confidentially since PGP combines public key and private key encryption. The sender encrypts all the messages by using the public encryption algorithm provided by the user.
- It provides message authentication and integrity checking. Integrity checking means it checks whether the message was sent by the claimed sender or not and also detects if a message has been altered after it was written or not.
- It also ensures and checks whether the message belongs to the intended recipients or not.
Advantages of PGP encryption
Let’s see some of the advantages that are listed below of PGP Encryption.
- Any type of information can be shared securely with others whether it be an entire department or a group of users.
- Emails cannot be attacked by hackers or any type of email attack, they will be secure.
- Once the files are deleted, they cannot be recovered by others.
- PGP verifies the information of the sender, to ensure that the email was not intercepted by a third party.
- All sensitive information is always protected. No one from the internet can view it and steal it. PGP assures that information has been sent from the sender side, the same has been received from the receiver side all, and no types of modifications have been done in between.
- Users need no training to learn how the PGP encryption software works. These are very easy to learn how to use.
Disadvantages of PGP Encryption
Following is the list of disadvantages of using PGP Encryption.
- It is not user-friendly and it’s the biggest disadvantage of PGP Encryption. Encrypting the message with PGP Encryption takes time and effort, which complicates the message sent by the user.
- It is not a compatible software program, which means if the message is to be sent with PGP Encryption it’s mandatory to have the same version of the software at both ends.
I hope this wonderful concept related to security and privacy concerns is very much clear to all, and now you all must be freely working over the internet. For much more exciting modules, stay connected with us. Until then, Stay happy, stay safe, keep reading, and enjoy learning.