Hello, everyone, Welcome back. In this module, I will be discussing what is Digital Signature Standard (DSS in Cryptography) is. So, without further delay, let’s begin.
What is Digital Signature Standard [DSS in Cryptography]?
Digital Signature is a way to validate the authenticity and integrity of the message or digital or electronic documents. Authenticity means to check whether the data is coming from a valid source or not to the receiver i.e. to verify the identity of the sender and integrity means to check that the data or message should not be altered during the transmission.
DSS or Digital Signature Standard was introduced by the National Institute of Standards and Technology (NIST) in 1994. It has become the United States government standard for electronic document authentication. The Federal Information Processing Standard (FIPS) 186 specifies the DSS. It was first proposed in 1991 and revised in 1993 as a result of public concerns about the scheme’s security.
DSS employs SHA (Secure Hash Algorithm) to create digital signatures and offers a new digital signature mechanism known as the Digital Signature Algorithm.
What is the DSS approach in Cryptography?
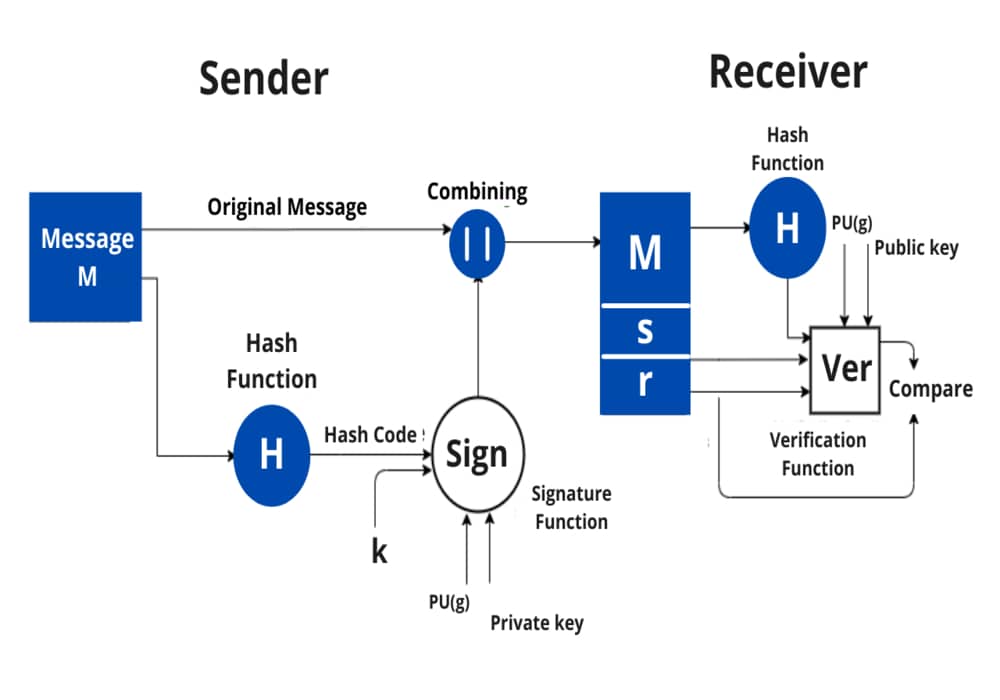
The DSS is different in the fact that the RSA algorithm uses the public key, private key and hash function whereas the DSS uses the public key, private key, hash function, a random number k, and global public key. Therefore, DSS provides more security than RSA algorithms.
A hash code is generated from the message and given as input to the signature function on the sender side. The other inputs to a signature function include a unique random number k for the signature, the private key of sender PR(a), and the global public key i.e., PU(g).
The output of the signature function consists of two components: s & r, which are concatenated with the input message and then sent to the receiver.
Signature = {s, r}.
On the receiver side, the hash code for the message sent is generated by the receiver by applying a hash function. The verification function is used for verifying the message and signature sent by the sender. The verification function takes the hash code generated, signature components s and r, the public key of the sender (PU(a)), and the global public key.
The signature function is compared with the output of the verification function and if both the values match, the signature is valid because A valid signature can only be generated by the sender using its private key.
Let’s see what the steps involved in DSS in Cryptography are.
What are the steps involved in DSS in Cryptography?
- Generation of keys i.e., public and private keys for the source.
- Creation of digital signature by the source for a message.
- The receiver verifies the digital signature.
The DSA (Digital Signature Algorithm)
1. Generation of a global public key component
- Find a prime number p such that 2^L-1 < p < 2^L, where L is an integer between 512 and 1024 i.e., 512 <= L <= 1024.
- Find another number q which is a prime divisor of (p-1).
- Compute g = h^(p-1)/q mod p, where h is an integer between 1 < h < p-1 and g should be greater than 1 or h^(p-1)/q mod p>1.
2. Finding the user’s private and public keys
- The private key, x is any random number such that 0 < x< q.
- The public key, y = g^x mod p
3. Generating the Signature
- Finding the components of signature s and r.
- r = (gk mod p) mod q
- s = [k^ -1 {H(M) + x*r}] mod q where k is an integer such that 0 < k <q.
- Signature= (r, s)
4. Verifying the signature
Let M’, r’, and s’ be the message and signature components respectively received corresponding to M, r, and s.
To verify whether the signature is valid or not, first, the following condition needs to be checked:
0 < r’ < q and 0 < s’ < q
If any of the above conditions are not met, the signature is considered invalid and is therefore discarded; otherwise, if both conditions are met, the following parameters are computed:
v = [(g^u1 y^u2) mod p] mod q
u1 = [H(M)w] mod q
u2 = (r’) w mod q
w = (s’)^ -1 mod q
Test: v = r’
If v = r’, the signature is correct; otherwise, the data or message has been altered.
I hope this module will be useful and that you now have a good knowledge of what is Digital Signature Standard (DSS in Cryptography). Stay tuned for more instructive and engaging modules like this.