Hey folks, welcome to this module, we are going to discuss What is decryption techniques and What is encryption techniques? What are they? How they do work?
So, let’s see into the depth of the What is Decryption Techniques module and gain some knowledge.
What is Encryption and Decryption Techniques?
We all work on the internet, communicate through the internet, and want our data and information should be secured, and it is done by cryptography. Cryptography prevents other users and attackers from accessing our confidential data and information. The two essential functionalities of cryptography are encryption and decryption. Let’s learn about the same in more detail.
What is Encryption Techniques?
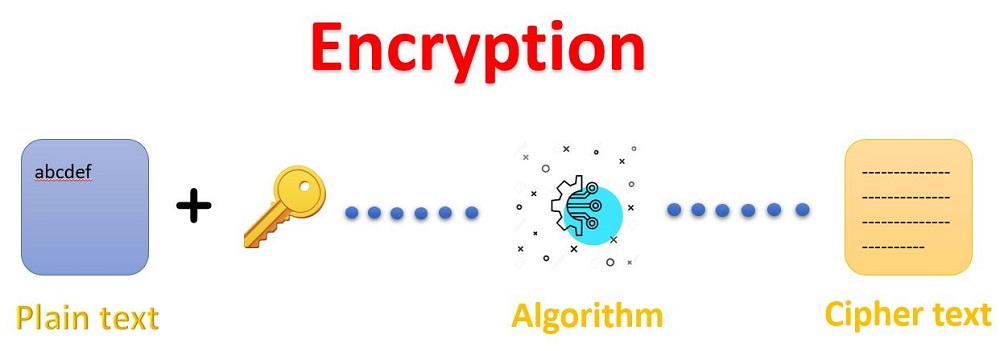
Encryption techniques is the process that converts the original message sent by the sender into an unrecognizable form so that no one from the network can read or understand it. It converts the normal message i.e., plain text into a meaningless or useless message i.e., ciphertext. This new form of message, i.e., the unrecognizable form is totally different from the original message. This is the reason that attackers and many external agents are not able to read the data as senders send the data by using an encryption algorithm. It takes place at the sender’s end. The message can be encrypted easily by using the secret key or public key.
The below diagram depicts the clear process of how the encryption technique is applied and the original message and data are converted to the ciphertext.
What is Decryption Techniques?
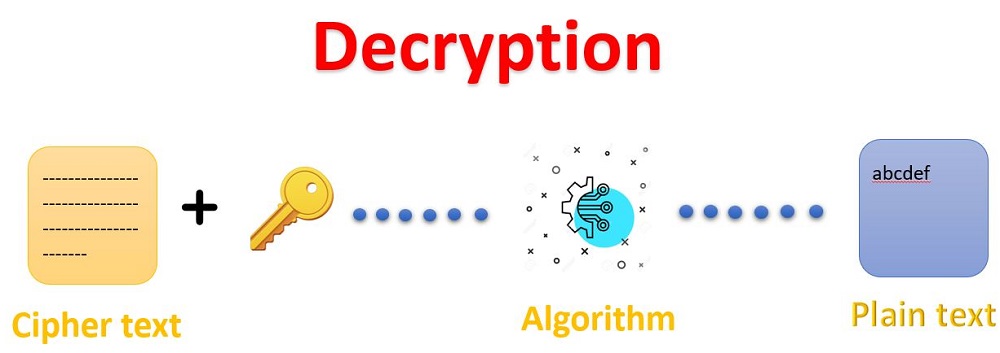
Decryption techniques is the process in which the encrypted code or data is converted back to a form that is easily understandable and readable by a human or machine. This is basically known as decoding encrypted data. It takes place at the receiver end. The message can be decrypted either with the secret key or the private key.
The below diagram clearly shows the decryption technique and also the encrypted text i.e., the ciphertext is converted back to the original message.
What are the types of Keys available?
There are some key presents that help in performing the encryption and decryption technique. Let’s see in more detail about the keys available.
Symmetric Key
This key helps in performing Symmetric Encryption also known as the Symmetric-key encryption algorithm. It uses the same cryptographic keys for performing both the encryption of plaintext from the sender’s side and the decryption of the ciphertext on the receiver side.
Asymmetric Key
Asymmetric key encryption algorithm uses two pairs of keys, which are used for encryption. These two different keys are used for encrypting the data and for decrypting the data. The public key is made available to anyone whereas the secret key is only made available to the receiver side of the message. This provides more security as compared to symmetric key encryption.
Public Key
Public keys are the keys that are basically used to encrypt the message for the receiver. This cryptography is an encryption system that is based on two pairs of keys.
Private Key
The private key usually used with the asymmetric encryption algorithm as one can use the same key for encrypting and decrypting the data. It also may be a part of the public/private asymmetric key pair.
Pre-Shared Key
It also known as PSK, is a shared secret key that was earlier shared between two different organizations or people using a secure channel before it is used.
Why use encryption and decryption Techniques?
Let’s focus on some of the important reasons for using encryption. Here some of them are mentioned why use encryption and decryption techniques.
- It provides confidentiality to our private data and information and for particular organizations.
- It helps in protecting or preventing plagiarism and thus protects the IP.
- It helps in protecting our important data such as our user ID, password, and login ID, which are very confidential.
- It is a very essential and useful method for the organization or company as it helps to protect the data from outsiders and no one can able access the data. It provides security.
- It also helps you to ensure that no one can able to modify or alter the data or file.
It is very helpful over the internet as most of us work on the internet, and where an attacker can easily access your data, so in order to prevent this, we use the encryption technique.
I hope the What is decryption techniques and What is encryption techniques? the module was very useful and understandable to all and you all must enjoy reading the module and gain a lot of knowledge about what is encryption and decryption techniques. For many more amazing modules stay connected with us. Until then keep learning, keep reading, and stay safe.