Hey guys, welcome back. In this module, I will be discussing the Message Authentication Code (MAC) in Cryptography. After reading this module, you will get to know what message authentication is and it’s working. Without further delay, let’s find out what it is.
Message Authentication Code (MAC) in Cryptography
A message authentication code or MAC is a security code or tag that is appended to the message sent by the sender to the receiver for providing message authentication and integrity (no alteration in message). It is similar to Message Digest (MD) except that it uses the symmetric key cryptography process to authenticate a message i.e., the same key is shared between sender and receiver. The keyed hash function is another name for the message authentication code. MAC is also referred to as Cryptographic Checksum.
MAC = C (K, M), where K is a shared secret key and M is a message to be authenticated.
A message authentication code (MAC) algorithm takes a message to be authenticated & a secret key that is known only to the sender of the message and the receiver of the message & produces a MAC as an output. By using MAC, a receiver can check the integrity of the message & authenticity of the message i.e., whether it is coming from the correct sender or not. MAC does not provide Non-Repudiation.
In electronic money transfers, message authentication codes (MACs) are employed to ensure information integrity.
Now, let’s see the types of message authentication code (MAC) in Cryptography.
What are the different types of Message Authentication Codes (MACs)?
There are four different types of Message Authentication Codes:
- Unconditionally secure
- Hash-function based
- Stream Cipher-based
- Block Cipher-based
How message authentication code (MAC) works?
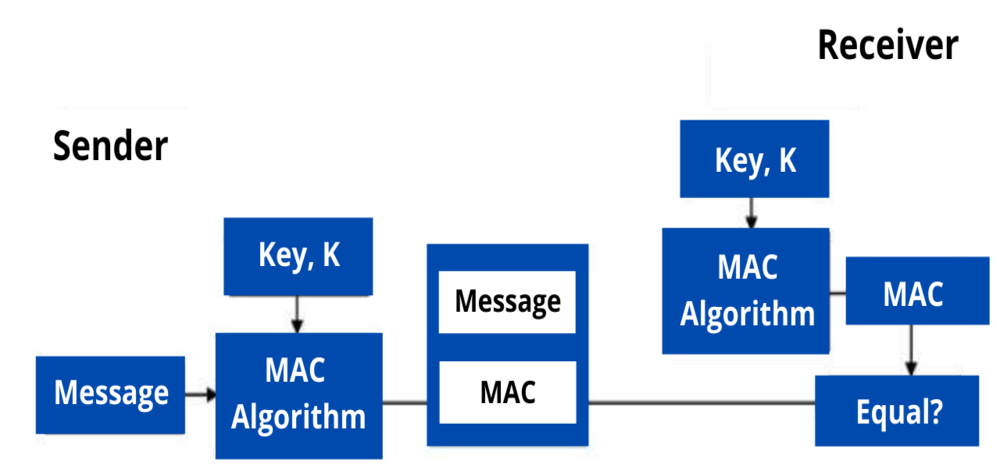
There are four important components used for generating a Message Authentication Code (MAC):
- The message of arbitrary length
- Key
- MAC algorithm
- MAC value
The sender and receiver share the same secret key to produce a Message Authentication Code or Cryptographic Checksum. This generated MAC is appended to the message and sent to the receiver. At the receiving end, the receiver also generates the Message Authentication Code (MAC) with the same shared key which is compared with the MAC generated by the sender. If both the MACs are equal, then the message is valid and coming from the correct sender, otherwise, the message is invalid.
A message’s hash value would be different if a sender didn’t know the secret key, indicating to a receiver that it wasn’t from the original sender.
Now let’s know one type of Message Authentication Code, HMAC.
What is a Hash-Based Message Authentication Code (HMAC)?
Hashing Based Message Authentication Code (HMAC) is one the type of Message Authentication Code. It is obtained by executing a cryptographic hash function on the message to be authenticated and using a secret shared key. SFTP, FTPS, HTTPS, and other transfer protocols rely on HMAC to check the integrity and authenticity of data. MD-5, SHA-1, or SHA-256 are some of the cryptographic hash functions that can be used.
HMAC is quite similar to Digital signature since both of them use a hash function and a shared key, but the difference between them is that HMACs utilize symmetric keys (same key) whereas Digital Signatures use asymmetric keys (two different keys).
In HMAC, the original message is converted into a message digest (MD) using any of the cryptographic hash functions such as MD-5. The message digest (MD) is then encrypted using a shared secret key and at last, it is appended to the message or data.
In brief, a Message Authentication Code or MAC is a security tag that is attached to the message to be authenticated to provide integrity of data or message sent by the sender to the receiver. Unconditionally secure, Hash-function based, Stream Cipher-based, and Block Cipher-based are the types of Message Authentication Codes (MACs). A lot of protocols make use of Message Authentication Codes.
I hope this module has provided you with the basic knowledge needed for Message Authentication Code (MAC) in Cryptography and have known about its types. You can visit our website, for a more informative module like this.