Hi, guys, welcome back. In this module, I will discuss what is DES (Data Encryption Standard) Algorithm is. After reading this module, you will get to know the various steps involved in the DES (Data Encryption Standard) Algorithm, why to learn it, its implementation, and modes of operation. Let’s continue to know it, then.
What is DES Algorithm?
At the start of the 1970s, the IBM team created a symmetric-key cipher block algorithm known as DES (Data Encryption Standard) Algorithm. The term symmetric key means that the same key is used for encryption & decryption of plain text or message. The National Institute of Standards and Technology (NIST) later adopted this algorithm.
The DES algorithm takes the plain text of 64-bit as input & produces a ciphertext of 64-bit using a key of 56 bits. Initially, a 64-bit key length is used but an 8-bit is discarded.
The Data Encryption Standard (DES) was discovered vulnerable to powerful attacks and hence DES has slightly declined in use. The 56-bit key length used in DES makes it unsafe against cyber attacks like brute force because the 56-bit key length requires 2^56 attempts for an attacker to find the correct key, which is not enough to protect sensitive data against brute-force attacks with modern computers. So, in May 2005, the Data Encryption Standards (FIPS 46-3) was officially withdrawn.
The triple DES or 3DES algorithm is a DES algorithm example that was approved for government-sensitive information or data until 2030. Now, let’s see how the DES algorithm works.
How does the DES Algorithm work?
DES is a Feistel Block Cipher implementation, known as LUCIFER. It uses a Feistel structure with 16 rounds, where a different key is used for each round.
The DES algorithm steps are given below:
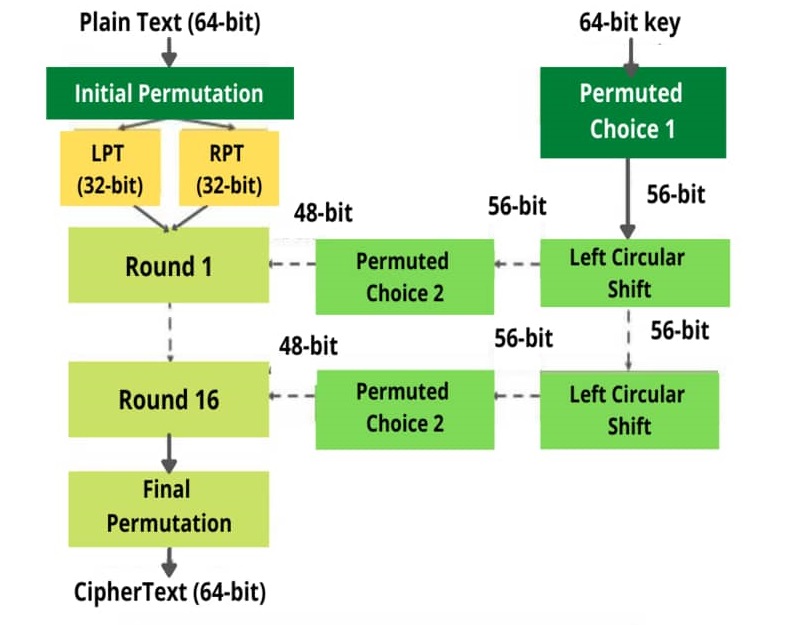
- The process begins by giving 64-bit plain text as input to an initial permutation function (IP).
- The initial permutation (IP) is then carried out on plain text.
- The initial permutation (IP) generates two halves of the permuted block, known as RPT (Right Plain Text) and LPT (Left Plain Text).
- Each Left Plain Text (LPT) and Right Plain Text (RPT) is encrypted through 16 rounds.
This encryption process consists of five stages:- Key Transformation
- Expansion permutation
- S-box permutation
- P-box permutation
- XOR & Swap
- Finally Left Plain Text (LPT) is combined with Right Plain Text (RPT). After that, on the newly combined block generated, a final permutation is performed.
- The output of this process will produce a 64-bit ciphertext.
The method of decryption uses the same algorithm, but it is done in reverse order of the same key as the DES algorithm is the symmetric key algorithm.
What are the disadvantages of the DES Algorithm?
- The total number of 16 rounds in DES makes the algorithm complex.
- DES was mainly designed for hardware so it runs relatively slow on software compared to hardware.
- The 56-bit key length used in DES makes it possible to decrypt the encrypted code with modern technologies. Moreover, it can be broken using brute-force attacks and linear cryptanalysis. Hence, AES (Advanced Encryption Standard) has replaced the DES (Data Encryption Standard).
What are the advantages of the DES Algorithm?
- DES was developed in 1977 to run on hardware, hence, this algorithm works fast in hardware.
- DES is relatively easy to implement because of its Feistel structure and basic or uncomplicated logic.
- The same algorithm is used for both encryption & decryption by just reversing the order of 16 round keys.
Why learn DES Algorithm?
One of the main reasons to learn DES (Data Encryption Standard) is that it forms the foundation for encryption algorithms. This makes it easy for one to understand the implementation or working of currently used encryption algorithms or methods, which are much faster than the DES algorithm.
Let’s see what are the modes of operation of the DES Algorithm.
What are the modes of operation of the DES Algorithm?
DES uses five different modes of operation.
- ECB (Electronic Code Book)
- CBC (Cipher Block Chaining)
- CFB (Cipher Feedback Block)
- OFB (Output Feedback Block)
- CTR (Counter)
How to implement the DES algorithm?
For implementing DES (Data Encryption Standard), one needs to select a security provider. The selection depends on the programming language used such as MATLAB, C, Python & Java.
Once you select a security provider, you need to select whether to use a plain text or byte array to produce a key by yourself or a random secret key created by the key generator.
After implementing the DES algorithm, one can test the algorithm by using GitHub recurrence relation.
I hope you have found the What is DES Algorithm module beneficial. For more interesting modules like this, you can refer to our website.