Hey folks, Welcome all, in this module we are going to talk about What is Secure Shell or (SSH)? We all work on the internet and communicate with others also, so we need security from various computer network attacks or some type of protocol that can provide the same. So, let’s move and read in-depth about the same.
What is Secure Shell or (SSH)?
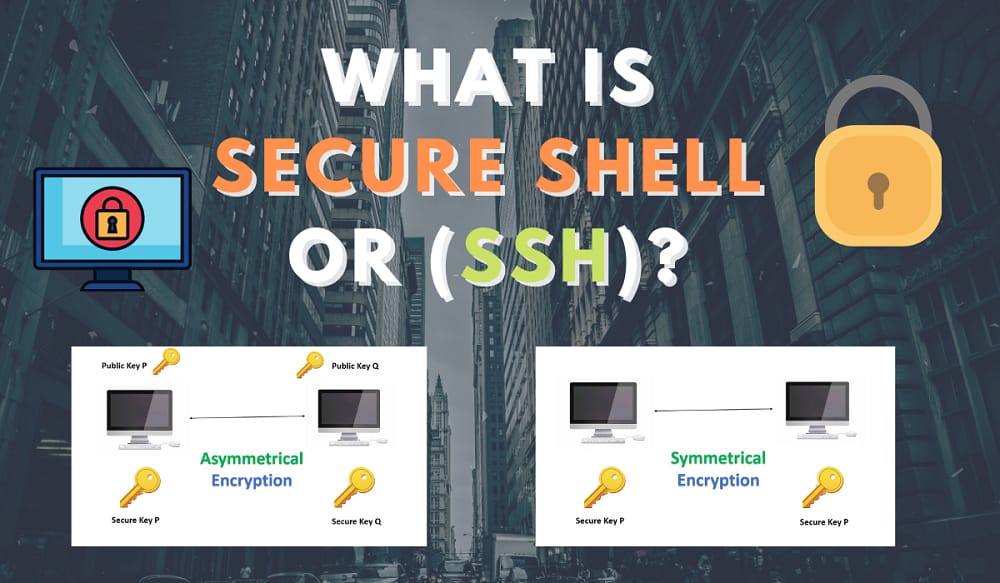
Secure Shell or SSH is the application layer protocol which is basically a 7 layer of the OSI model. It is the network protocol that allows one computer or system to connect with another computer or system securely over an unsecured network. So, they can freely communicate and share files and data. SSH allows us to connect remotely to the servers without having physical access.
A secure shell provides a public key authentication, a strong password authentication, and also secure data communications i.e., in an encrypted manner so that they both can freely work over the internet or an open network.
SSH is basically implemented as a client-server model, one system is the Client and another one stays host or server. It is also used to create secure tunnels for different other applications.
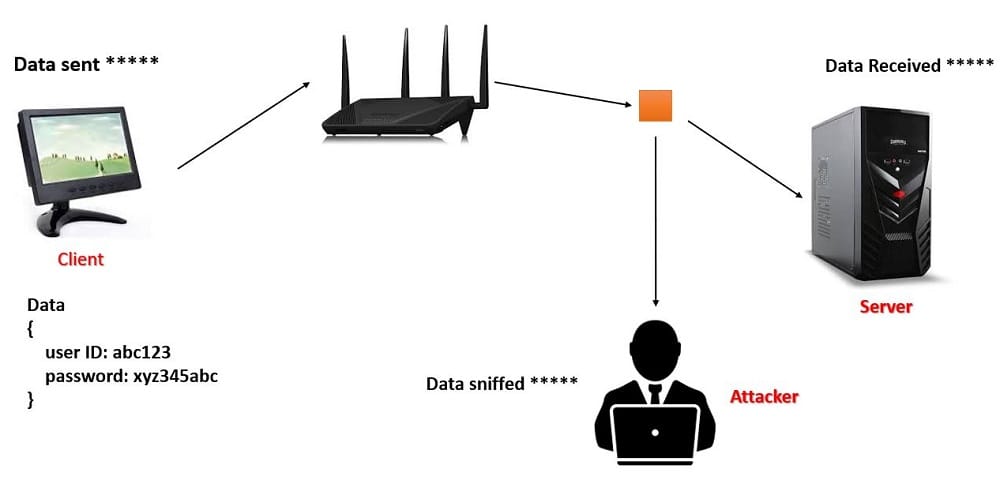
In the below figure, it’s clearly displayed that the data is transferred using encryption and thus cannot be read by the attacker.
It was designed to replace the telnet protocol that is also used to transfer the data but without encryption and is also an application layer protocol. Without encryption means anyone from the internet can easily see your data that all are getting transferred. The data travels in plain text when it is not encrypted whereas SSH transfers the data in an encrypted manner through a tunnel, no one can identify that what data is being transferred however it can be determined that the data is being transferred and how much the data is being transferred.
What is the difference between HTTP and SSH?
There is also another protocol that transmits data with encryption and that one is HTTP i.e HyperText Transfer Protocol, the only thing is HTTP allows web browsers with servers to display the websites, whereas in SSH data communicate or get exchanged between two systems and is done by shells, not just a server and a browser. Through shells, you can also talk to an Operating System.
Windows command prompt or a Linux terminal all are shells, to which you can execute all the commands on the machine you are connected to. And you are talking to the operating system when you are connected to the command prompt or a terminal line.
What can be Transferred using SSH?
SSH can be used for the following:
- Commands Transfer
- Text Transfer
- Data Transfer
- Files Transfer (It takes place using the encrypted version of File Transfer Protocol which is using SFTP i.e., secure file transfer protocol)
These are the things that can be transferred using SSH securely.
How does SSH work?
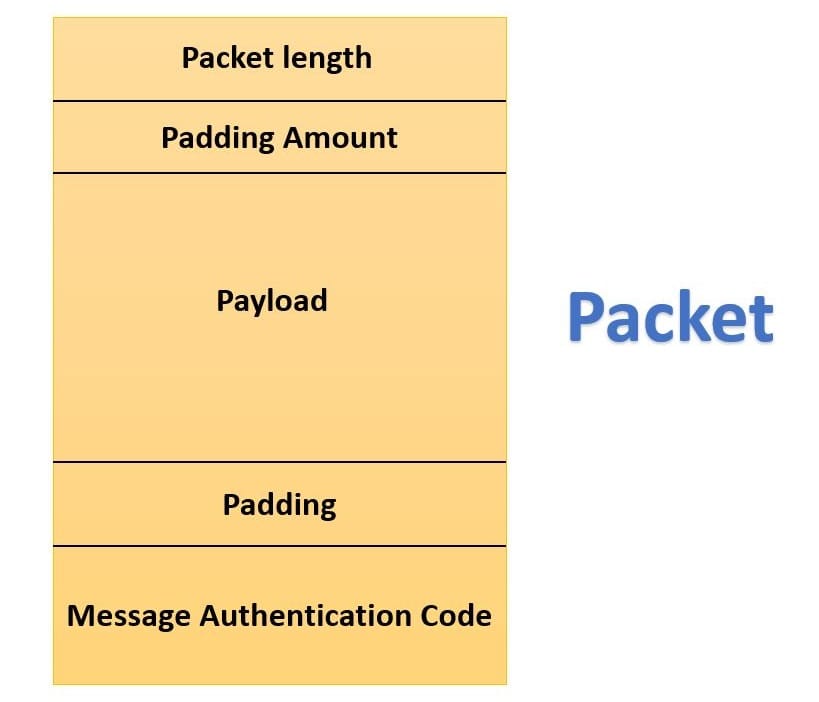
Firstly, the data is broken down into many different packets, this packet consists of many fields. At the top, packet length is there, which tells us what is the length or the size of the packet after that another field is there and i.e., padding amount. Then the payload is there, then again padding comes. Finally, at the last, we have a message authentication code, which tells us that our data is secure refer to the following diagram mentioned below.
This packet is then transferred to the server, the server has to decrypt the packet to extract all the data from the packet. The same process is carried out for each and every single packet that has to be transferred over the internet.
What techniques are used by SSH?
To enable a secure connection. SSH uses three different types of techniques at various points. The three techniques used by SSH are.
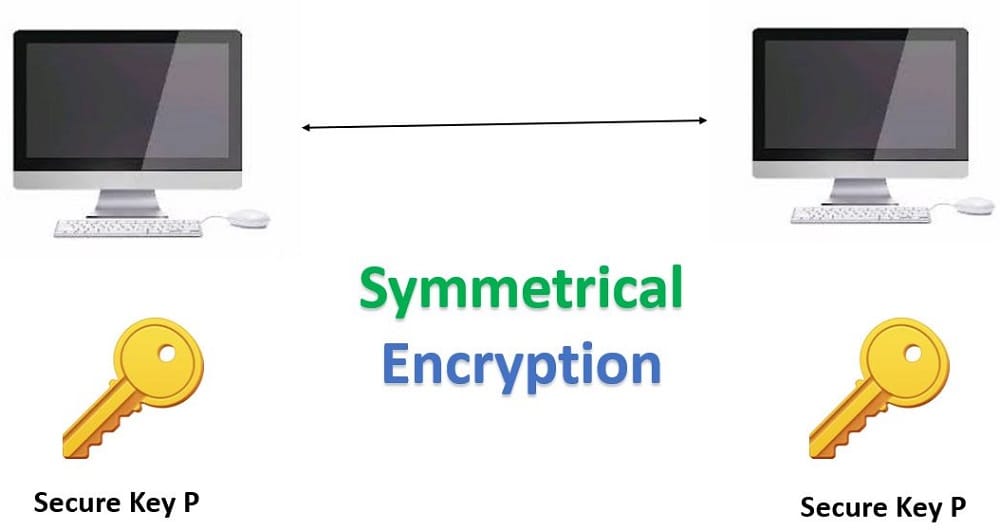
Symmetrical Encryption Techniques
Symmetrical Encryption is also called shared key encryption or shared secret encryption. In this, only one key is used by both the destination port and the source port and that key is used to encrypt the message that has to be sent to the destination and decrypts that message received at the destination. It encrypts the entire SSH session and a specific key is used at each SSH session.
The key exchange algorithm should be used because it provides a secure way to exchange the secret key without any interception.
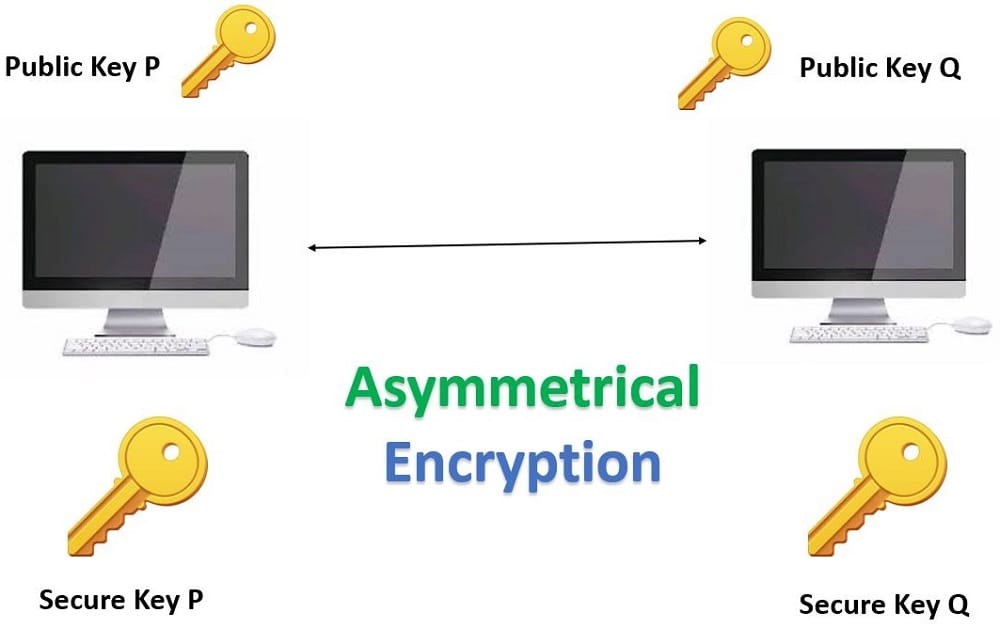
Asymmetrical Encryption Techniques
Asymmetrical Encryption uses a key pair concept i.e., a public key and a private key. They use two different separate keys for encrypting the message and for decrypting the message, a public key, and a private key. A public key can’t be shared with anyone but a public key can. A public key is stored in the SSH server whereas a private key is stored in the SSH client.
You can send a message by encrypting that message with my public key and I can only decrypt that message with my private key.
Hashing Techniques
Hashing is a one-way process and it is not meant to be decrypted. It is another form of cryptography. That uses a secure shell connection. It creates a signature or summary of a set of information. SSH uses hash-based Message Authentication i.e., HMAC, and ensures that the message that is sent should be received in a complete and unmodified form.
The message that is transmitted using a hash function must contain something called MAC. This MAC is nothing but a hash generated from the packet sequence number, symmetric key, and the message contents that were already sent.
What are the Advantages of SSH?
The following listed are the advantages provided by SSH.
Authentication
SSH easily figures out user identity, i.e., to avoid attackers to get inside the system. It implements password authentication and private key authentication which makes it more secure and more reliable.
Avoid attacks
SSH prevents connections with attacks such as DNS spoofing, IP spoofing, etc. When the attackers try to get inside your connection to destroy your data, then immediately SSH destroys the connection.
Hosting Control
SSH also gives this advantage like controlling the accounts of the host directly on the web server, which is very easy and also saves a lot of time. SSH supports the remote server control and thus allows the user to easily do some management like data transfer, server rebooting, configurations of accounts, and many more.
What are the disadvantages of SSH?
The following mentioned are some of the disadvantages of SSH.
- If the DNS is not available at that particular moment or the source IP address does not resolve, then it takes delay during the authentication.
- It is slightly somewhat complex to the administrators.
I hope you all gained a lot of meaningful knowledge from What is Secure Shell or (SSH)? module and got more excited to know about the various fields of cryptography, So, for more modules like this, stay connected with us. Until then, Happy Learning, Stay Happy, Stay safe.